The DDoS Attack That Crashed Major X: Uncovering the Hidden Truth Behind the Widespread Outage
The recent widespread DDoS attack that crashed Major X's website was a stark reminder of the ever-present threat of cyberattacks on online businesses. For many users, the website was unavailable for hours, resulting in significant financial losses and damage to the company's reputation. However, the question on everyone's mind is: what really happened behind the scenes of this devastating attack? In this article, we will delve into the hidden truth behind the DDoS attack that crashed Major X, exploring the tactics used by the attackers, the measures taken by the company to mitigate the attack, and the long-term consequences of this cyberattack.
The Rise of DDoS Attacks: A Growing Concern for Businesses
DDoS (Distributed Denial of Service) attacks have become increasingly common in recent years, with many businesses feeling the brunt of these attacks. According to a report by IBM, the average cost of a DDoS attack is estimated to be around $2.3 million, with some attacks reaching as high as $18 million. The severity of DDoS attacks lies in their ability to overwhelm a website's resources, making it inaccessible to users. This not only results in financial losses but also damages a company's reputation and erodes user trust.
The Anatomy of a DDoS Attack
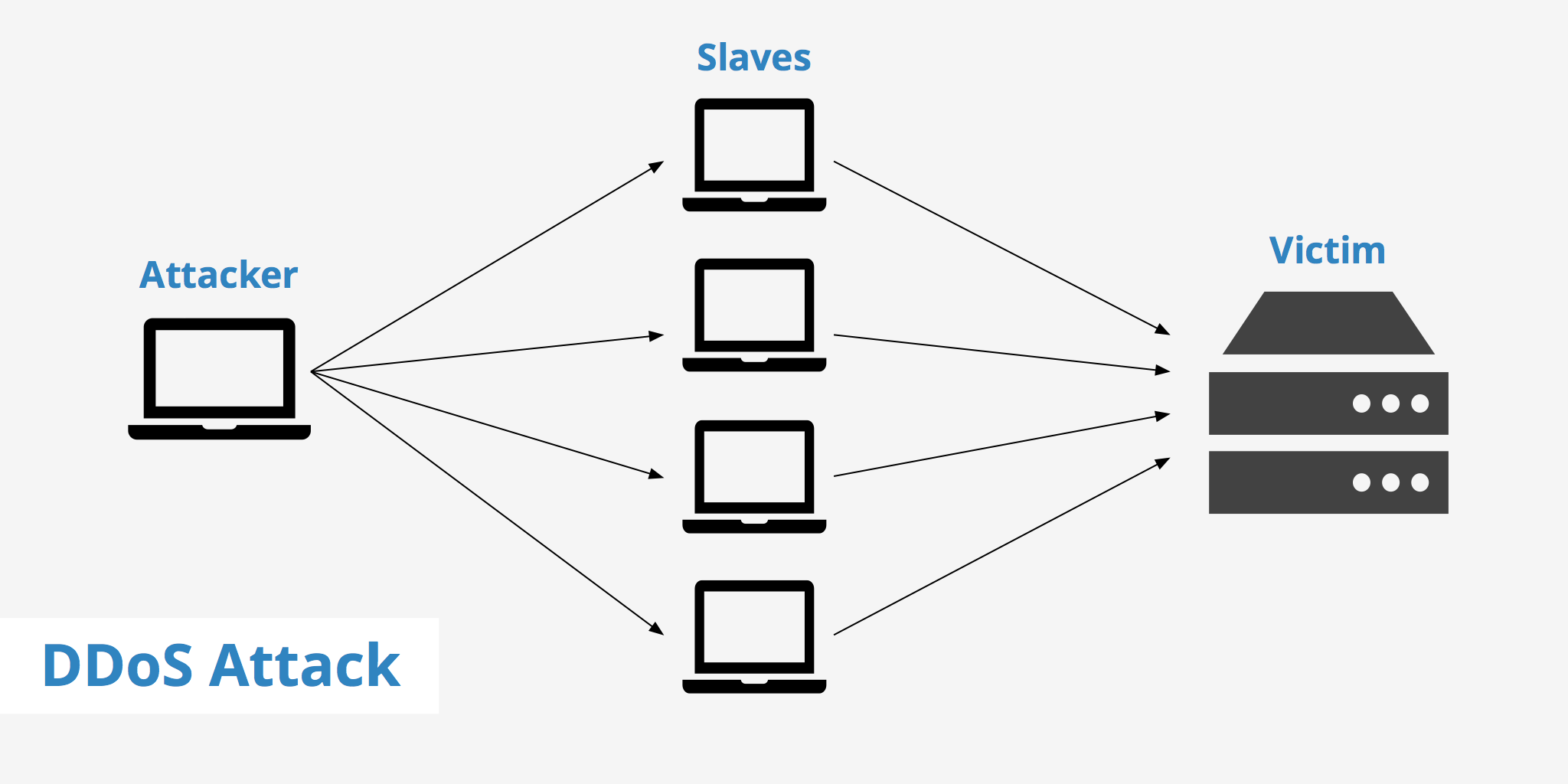
A DDoS attack typically involves three key components: the attack vector, the botnet, and the command and control server. The attack vector refers to the entry point used by the attackers to launch the attack, which can be a vulnerability in the website's code or a weak point in the network infrastructure. The botnet is a network of compromised devices, often malware-infected computers or smartphones, that are used to launch the attack. The command and control server is the central hub that coordinates the attack, receiving instructions from the attackers and sending commands to the botnet.
The Tactics Used by Attackers
Attackers use various tactics to launch a successful DDoS attack. These include:
- Syn flooding: This involves flooding the website's servers with fake requests, causing them to become overwhelmed and inaccessible.
- Amplification attacks: This involves exploiting vulnerabilities in network protocols, such as DNS or NTP, to amplify the attack.
- Application layer attacks: This involves exploiting vulnerabilities in web applications to launch the attack.
Measuring the Impact of a DDoS Attack
Measuring the impact of a DDoS attack can be challenging, but it is essential to understand the scope of the attack. Some common metrics used to measure the impact of a DDoS attack include:
- Bandwidth: The amount of data transmitted during the attack.
- Packet loss: The number of packets that are lost or dropped during the attack.
- Response time: The time it takes for the website to respond to user requests.
Mitigating the Impact of a DDoS Attack
To mitigate the impact of a DDoS attack, companies can use various strategies, including:
- Content delivery networks (CDNs): CDNs can help distribute the traffic, reducing the load on the website's servers.
- DDoS protection services: DDoS protection services can help detect and mitigate the attack.
- Network segmentation: Network segmentation can help isolate the affected servers and prevent the attack from spreading.
The Response to the DDoS Attack
When Major X's website was hit by the DDoS attack, the company's IT team sprang into action to mitigate the attack. The team worked closely with their internet service provider (ISP) to identify the source of the attack and develop a plan to stop it.
The Role of the ISP
The ISP played a critical role in the response to the DDoS attack. The ISP's network engineers worked closely with Major X's IT team to identify the source of the attack and develop a plan to stop it. The ISP also helped to block the traffic from the botnet, preventing further attacks.
The Use of DDoS Protection Services
Major X also used DDoS protection services to mitigate the attack. The services helped to detect and block the traffic from the botnet, preventing further attacks.
The Long-Term Consequences of the DDoS Attack
The DDoS attack had significant long-term consequences for Major X. The company's website was unavailable for hours, resulting in significant financial losses and damage to the company's reputation. The attack also led to a significant increase in user complaints, which further damaged the company's reputation.
The Need for DDoS Protection
The DDoS attack on Major X serves as a stark reminder of the need for DDoS protection. Companies must take proactive measures to protect themselves against DDoS attacks, including:
- Implementing DDoS protection services
- Conducting regular security audits
- Training employees on cybersecurity best practices
Best Practices for DDoS Protection
To protect against DDoS attacks, companies can follow several best practices, including:
- Monitoring network traffic
- Implementing rate limiting
- Using security information and event management (SIEM) systems
- Conducting regular security audits
The Future of DDoS Protection
The future of DDoS protection is rapidly evolving. Companies must stay ahead of the curve by investing in the latest technologies and best practices. This includes:
- Implementing machine learning-based DDoS detection
- Using cloud-based DDoS protection services
- Conducting regular security audits and testing
By staying informed about the latest trends and best practices, companies can protect themselves against DDoS attacks and minimize the impact of these
Chaun Woo Parents Nationality
Brad Pitt Height In Feet
Zoechip
Article Recommendations
- Loving Auntic Free
- Honey Toon
- Adrian Williams Wife
- Morgan Vera
- Lyna Perez
- My Pillow Net Worth
- Amerigo Vespucci
- Denzel Washington Trump
- Lina Medina
- Kim Kardashian Piddy